
Cyber security through post quantum crypto
The quantum computer offers opportunities for companies. And at the same time it raises questions among entrepreneurs. Is my data still secured? What risks do I run? When should I migrate and where to? And which software will I have to replace? At TNO we help organizations make networks quantum-safe and solve legacy problems.
Opportunities and risks of the quantum era
The quantum computer can contribute to new products and services. Solving problems that are practically unsolvable for current computers. And potentially even help develop personal medicines. However, we will also have to find an answer to the security risks that the quantum era entails. That is why securing information against attacks with a quantum computer is crucial. At TNO we help organizations to make networks quantum-safe in time, including for legacy systems. The quantum-safe Advanced Security Proxy is an example of the latter.
Post quantum crypto
Cryptography is widely used to protect information from unauthorized persons and to authenticate the sender of data. With success, because even the fastest computers would take hundreds of years to decipher encrypted information. This will change with the arrival of the quantum computer. It will take at least several years before there is actually a quantum computer that can crack today's cryptography. However, it is important to take action now.
Why start now?
All encrypted information that we now communicate, process or store can be saved and later cracked with a quantum computer. We call this a “harvest-now-decrypt-later” attack. It is therefore important to develop crypto systems now that are resistant to attacks with both current computers and quantum computers. Here we speak of post-quantum cryptography or quantum-safe cryptography. This way we keep confidential information safe for a long time. Another reason to start working on this now is the long migration path.
How do you make your organisation quantum-safe?
Limit the risk of quantum computers for cryptography within your organization. Download the new edition of the PQC migration handbook for concrete advice, guidelines and tools to carry out the migration.
Where do you begin with unravelling?
Within the company, it is often complicated to get a complete overview of the software, hardware and network traffic used and to determine whether the most recent cryptography is used everywhere. It is a huge job to figure this out and then make your systems safe again. Where do you start? With the inventory. This is a no-regret move, costs little time and money and provides good insight into the risks the organization runs. We can help you with that. The rise of quantum computing does not affect all cryptographic algorithms and applications equally. Curious? Our Quantum Risk Methodology for Cryptography paper is now available. Download the paper here (pdf)(in Dutch).
In collaboration, we have also developed the PQChoiceAssistant This tool helps organizations select the most suitable post-quantum cryptography scheme.
NIST Post-Quantum Cryptografie standards
The latest NIST Post-Quantum Cryptography standards have recently been released. These new standards are post-quantum: they are meant to resist future attacks that would use quantum computing, as the currently used methods based on factoring or discrete logarithm would become insecure when large-scale quantum computing becomes a reality. They are meant to replace or complement existing cryptography used ubiquitously in everyone's internet browser, phones, credit cards and contactless keys.
Check the latest NIST Post-Quantum Cryptography standards at this website.
Quantum-safe PKI
Public Key Infrastructure (PKI) is also affected by the quantum computer. This security instrument is widely used for digital authentication in all kinds of social applications, ranging from digital banking to exchanging information with the government. However, the migration to quantum-safe PKI is more complex than, for example, that to quantum-safe VPN, both on a technical and organizational level. TNO leads the public-private HAPKIDO consortium, which is investigating the migration to quantum-safe PKI.
Advanced Security Proxy
The Advanced Security Proxy (ASP) is a way to make organizations quantum-safe. It can help to inventory the security of software systems used. This is how legacy problems come to light. At the same time, the tool can overcome security risks by encrypting data exchange in a quantum-safe manner. And the ASP can improve the security of legacy (older) systems without editing these legacy systems themselves. It is somewhat like a smart VPN connection, except that the ASP stands between the network and the internet and can monitor all connections to the internet.
The benefits of Advanced Security Proxy
The question is whether legacy systems can handle post-quantum cryptography. They use larger keys or require more processor capacity than classical cryptography. The ASP quickly performs deep packet inspection on communication channels using programmable hardware. The tool performs various gateway functionalities. Consider monitoring the security level of the cryptography used. And upgrading cryptography to establish more secure channels that cross less secure networks like the Internet. By upgrading the encryption used, the ASP protects older devices and therefore legacy environments that cannot do this themselves.
ASP is cheaper and simpler
The ASP therefore protects older network systems against current security threats. This means that an organization does not have to immediately invest in major network updates. And that is a much cheaper solution, because the implementation costs of the ASP are low. It is also not necessary to update the entire security portfolio when you start working with ASP. The tool is a natural addition to your current security portfolio. With the ASP you can save a lot of costs. Especially as an organization with an extensive network infrastructure.
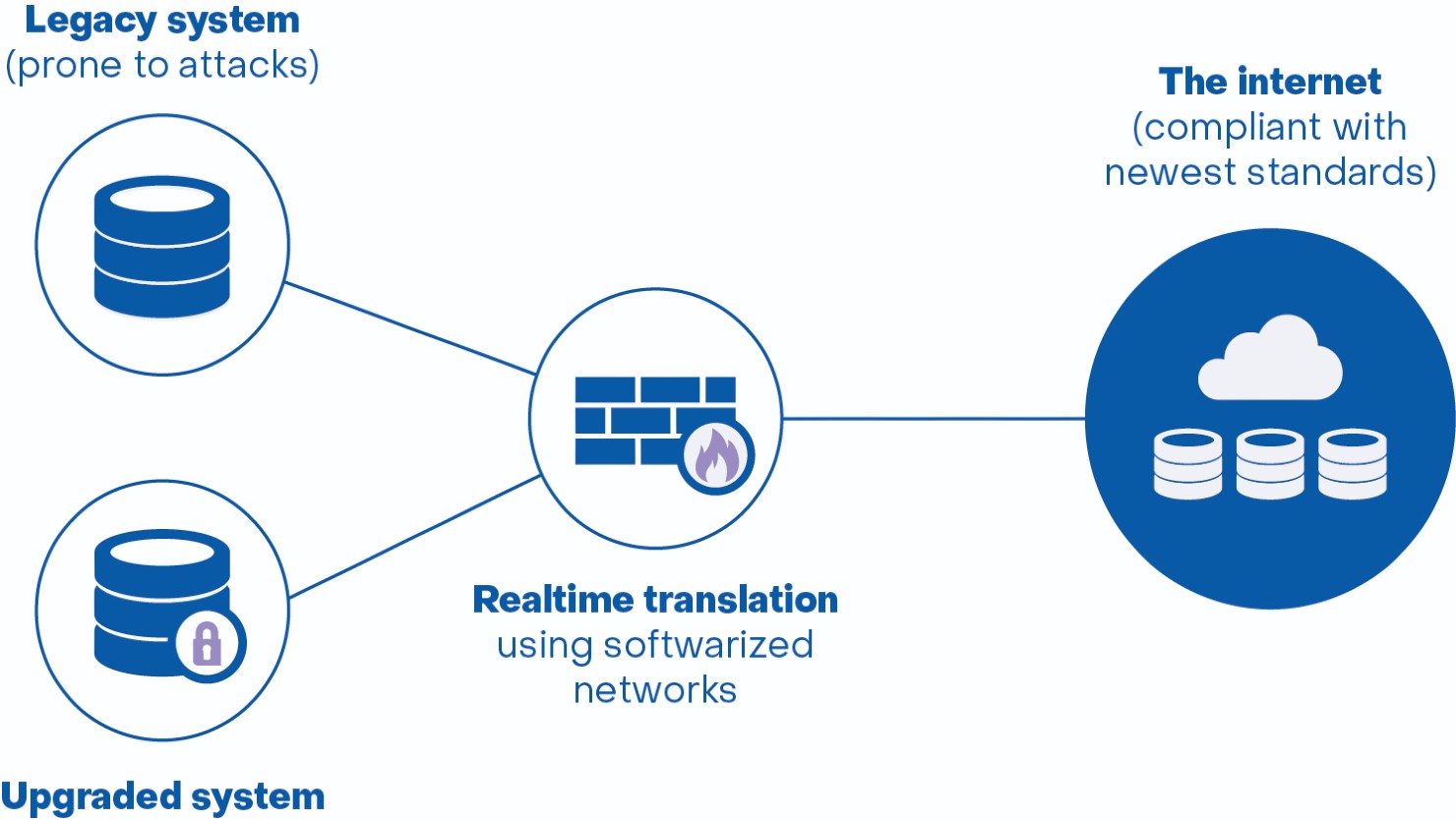
The ASP is somewhat like a smart VPN connection, except that the ASP stands between the network and the internet and can monitor all connections to the internet.
Quantum-safe VPN
VPN connections are often used. For example, to give people who work from home access to their employer's internal network. A VPN connection makes a secure connection to the employer's network over the internet from the home network. This is done via an encrypted connection. The cryptography used is currently not quantum-safe. And that entails a security risk. Because data that is currently exchanged via VPN connections is not protected against attacks with a quantum computer.
Post-quantum cryptography makes VPN connections quantum-safe. At TNO we tested this with OpenVPN. There are different types of post-quantum cryptography, each with different properties. Thanks to our tests, we know that some cryptography types require more bandwidth, while others require more computing power. It is important to investigate the impact of post-quantum cryptography for various security products. And which type is most suitable.
Interested in working with us?
Within TNO, there is a strong foundation of applied cryptographic knowledge and a great deal of expertise in the area of internet, communication networks and cybersecurity. This unique combination means that we can clearly overview the impact of post-quantum cryptography. And organizations can advise and guide them in the transition process of their information security. Would you like to know more about what TNO is doing in the field of quantum-safe cryptography? Contact us.
This can help your organization migrate:
- Download the new edition of the PQC migratie handbook (pdf) for concrete advice, guidelines and tools to carry out the migration.
- Use the PQCoiceAssistant tool to select the most suitable Post Quantum Cryptography scheme.
- Download the paper (pdf)Quantum risk methodology for cryptography.
Get inspired
Quantum Application Lab receives grant for quantum computing application development


Applied Cryptography & Quantum Algorithms

Quantum computing



