Self-sovereign identity: the good, the bad and the ugly
Self-sovereign identity (SSI) promises to empower citizens with new means to manage privacy, elimination of logins, and much faster transactions via the internet as well as in real life. SSI promises to empower organisations to speed up and automate transactions with customers, suppliers and partners, resulting in billions of euros savings on administrative costs, and higher customer satisfaction that results from better and speedier decision-making.
This blog illustrates the good side of SSI with a plethora of examples, comparing SSI-based business transactions with their current more cumbersome non-SSI equivalent. It also provides examples of the bad side, how SSI technology can be abused by unscrupulous organisations, and how a combination of technology, education and legislation could reduce this risk. It finally presents examples of the ugly side, how SSI technology can be used by criminals, and what type of countermeasures are conceivable.
SSI technology
SSI technology is explained in excellent detail elsewhere on the Internet (E.g. The Path to Self-Sovereign Identity, and references therein.), so we assume the reader is sufficiently familiar with its concepts, and we can focus on its main unique selling points:
- Pairwise trusted communication with any other citizen or organisation.
- Mutual verifiable credentials to speed up and reduce risk in transactions.
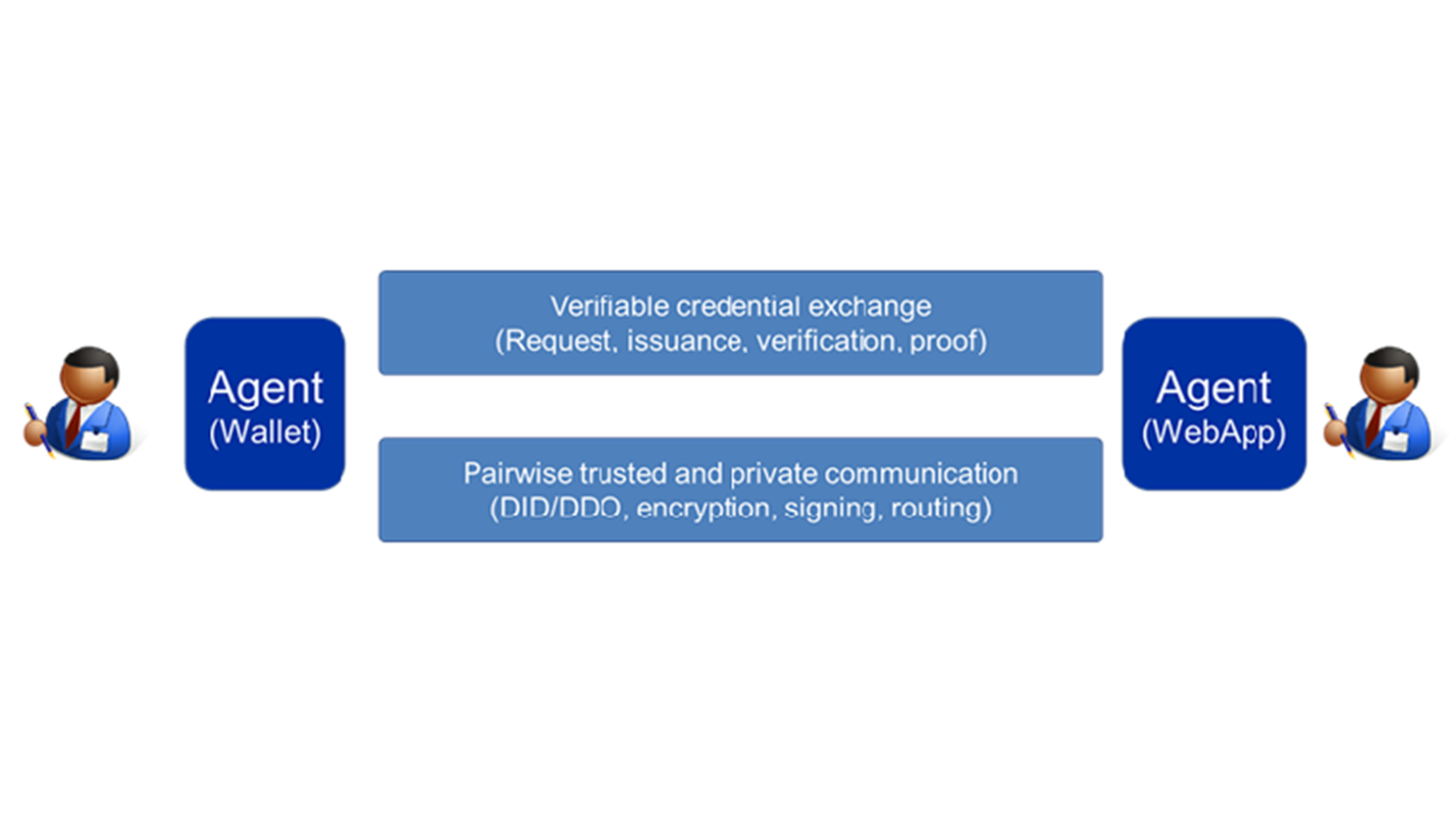
The first selling point is achieved with distributed identifiers (DID) and its associated resolution technology to obtain public keys and service endpoints in a DID document (DDO). For example, a web shop could publish a public DID/DDO to receive encrypted and signed communication from its customers, which a citizen could use to negotiate a DID-pair with that web shop that would enable either to set up private, secure and authenticated communications channels with the other at a later point in time, effectively making logins obsolete. Of course, all the required cryptography and communication stuff happen behind the scene inside the agents.
The second selling point is enabled with verifiable credentials (see Verifiable Credentials Data Model). For example, a patient receives medicines based on a recipe credential from a general practitioner, or an entrepreneur opens a business bank account using a credential of the chamber of commerce. Again, all the credentials and crypto stuff are kept behind the scene inside the agents, which use e.g. advanced cryptography (e.g. “zero-knowledge proofs”) to ensure that no information is leaked unnecessarily.
Essential to SSI are agents where all identity, cryptographic and credential information is securely stored and managed. For individuals such agents typically are typically apps (often called ‘wallet apps’) that run on a smartphone or tablet, preferably using a secure hardware module, protected by pin codes and biometrics, and have a secure backup in the cloud. Contrary to e.g. banking apps, they can be used for interacting with different organizations, across different domains, and countries. For organizations, agents are typically web services, that have ‘SSI functionality’ tacked on that allows not only users to fill in data, but also allowing agents of that user to fill in data in that same form.
The good: a much easier digital life
SSI technology empowers citizens, businesses, governments and other organisations by increasing convenience in managing your (digital) identity, by enhancing security, privacy and inclusion, by making organisations more efficient and effective, and by creating new jobs and businesses. They are explained below.
1. End-user convenience
No more username/password logins
How many times per day do you need to fill in a password? No more! Whenever you open a new account at a website using SSI, a new DID pair is created in your user agent application. At every subsequent communication with the same website, it uses the same DID pair behind the scenes, so no additional login is needed.
Account information no longer needs to include your personal information
Are you reluctant to create accounts with a web shop (or other web service) because it stores your personal information – including that of your credit card(s)? No more! Web sites no longer need to store any information that they could also obtain through verifiable credentials. That makes you safer, and the organization less vulnerable to breaches of (personal) data (and fines from privacy agencies).
Never type information in webforms again
How many times have you typed in your address, in order to get a parcel delivered to your house? No more! With SSI, the website asks your agent to share your postal address with the website. Your agent pops-up one or more addresses that it has stored. Most likely, you had already filled in a self-signed postal address, so you just select it, and the website automatically fills in the form. (H2020 TOOP refers to this as the “Once Only Principle”: type in information only once, see also Once-Only)
No more manual paperwork
How often do you need to obtain a formal document at one office (e.g. a medical specialist), and then present it to some other office (e.g. a health insurer) - possibly after having it converted into a PDF file? No more! With SSI, you can get your certificate-of-good-conduct, your parking permit, your driver’s license, your income statement, your China visa and many other in digital form. And you can present it electronically to whomever you want whenever you want.
No more wait time
How often do you need to wait a long time for some paperwork procedure to complete? No more! The presentation of verifiable credentials is electronic and immediate, which enables immediate automated electronic business decisions.
No more wrong documents
How often have you been sent back by some office, because you did not present the correct paperwork? No more! Electronic requests for verifiable credentials are accurately specified using semantic technology. So your user agent application knows exactly which of your verifiable credentials satisfy the request. And if you don’t have the right verifiable credentials, the request provides a precise specification to your user agent application from what issuers you can get the required credentials.
2. Security, privacy and inclusion
No more phishing and spoofing
How many times have you received phishing emails, or accidentally filled in your password at a spoofed website? No more! SSI-based communication is very secure, as a DID pair is useless to third parties, so you can no longer be phished into entering your password into a spoofed website.
Mutual authentication
How many times have you visited a website, and you were unsure whether you could trust it? No more! SSI works in both directions. Your user agent application asks the visited website for its credentials, and it can decide about its reliability based on your instructions, e.g. based on an independent quality mark for webshops.
No more spam
How often is your email address abused for spam? No more! All communication is compartmented via DID pairs. If a service provider starts spamming you via a previously established DID pair, you can instruct your user agent application to ignore it, so the service provider can no longer reach you.
More privacy
How often have you been asked to share more information than needed? No more! A hotel does not need your email address, phone number or passport number, but just enough information to enforce that you pay your bill. A disco or liquor store does not need to know your social security number, gender or date of birth, but just enough information to assure that you are old enough. SSI technology provides the citizen with accurate control which information is shared with whom.
Moreover, the compartmentalisation via DID pairs greatly enhances privacy. As you no longer need data-guzzling identity providers like Google and Facebook, they can no longer trace your steps via that route.
Better digital inclusion
How often do you need to help a “computer illiterate”, and use their login to help them? No more! The easier-to-use interaction (see above) makes SSI-enable transactions more inclusive. Moreover, SSI enables frameworks for guardianship and delegation of interactions and transactions, see for example the Sovrin Guardianship Taskforce. This eliminates the need for impersonation, and it provides proper provenance when guardianship and delegation are required.
3. Efficient and effective companies and organisations
Huge operational savings with lower validation costs and time
SSI promises huge cost savings. No more manual inspection of paperwork, e.g. authenticity checks with a magnifying glass. (Yes, there are hordes of people who spend their business hours checking authenticity of incoming paperwork). No more typing over information from scanned PDF documents. No more checking information that users entered at the website of authoritative registrations. It is estimated that the direct cost savings for validating information can be in the order of at least several tens of billions of euro in Europe annually.
Huge technical savings by reducing number of IT links
A significant source of cost in enterprise-IT is the creation and support of links between different IT systems. These links allow such systems to query data that the other system administers. A link is subject to maintenance whenever one of the systems it connects to is modified, or the data in one of these systems is changed. These links can be made obsolete whenever the systems issue attestations that contain the information required by other systems, thus saving the associated costs.
Happier customers, more business, less churn
The aforementioned benefits result in happy customers for commercial businesses, and hence more business and less churn. As such, SSI support will prove to be a unique selling point for those businesses compared to their non-SSI competitors. Happier citizens and better digital inclusion should also convince non-commercial and governmental organisations to use SSI solutions.
4. New jobs and new business
The creation and maintenance of SSI business ecosystems will result in new types of jobs, as well as new types of business. User agent applications need to be developed and integrated with novel secure hardware modules. Software, hardware and service infrastructure need to be developed and operated. New business models will be developed and exploited, for example for issuers of verified credentials; for developers and maintainers of sector-specific SSI governance frameworks; for SSI auditors and certifiers; for DID resolving providers, and for routing infrastructure providers for SSI-based trusted communication. Also, potential abuse and criminal use of SSI technology provide positive job and business opportunities to keep SSI business ecosystems secure and clean.
The bad: unscrupulous data guzzlers
SSI technology by itself is neutral, like any other technology. Its use determines its value to society. Some use may be considered bad.
Personal information has a lot of value. Self-provided personal information is now used by data guzzlers like Google and Facebook to provide targeted advertisements, to create information bubbles, and to share with third parties for their business decisions about you. Personal information will have even more value if it is not self-provided, but verifiably signed by a trusted issuer. SSI is designed to enable data-minimalism. That is, don’t ask for name, gender and date of birth, if your business decision only requires an older-than-18 check. However, existing and new data guzzlers will be tempted to a data-maximalist approach. SSI makes it very easy to share highly sensitive personal information. It makes it also easy to data guzzlers to ask for more information than they strictly need. Cookie-wall-like practices may be used to nudge a citizen to reluctantly accept and share more personal information than they should need to. Moreover, USA and China customs may feel tempted to ask visitors to hand over their full credential store from their smart phone.
Countermeasures will require a combination of technology, education, and legislation. Wallet applications need to be designed such that they properly inform users what information is requested and warn users if a request is deemed suspicious. This may include solutions for plausible deniability towards unreasonable data requestors. Education is needed to educate and warn citizens what information they don’t need to share. Legislation, e.g. GDPR, needs to be enforced to counter-act data-guzzling practices.
One idea is a bounty program. A good thing is that SSI requests cannot be repudiated. That is, a visitor can prove which information was requested by a website, at what time, and for which stated purpose. This proof will hold up in court, as the request is electronically signed by the verifier. A simple web shop may ask for your bank-account balance, your date of birth or your gender. Assuming that such information is legally immaterial to the web shop’s business decision to sell you something, you can file a complaint with a privacy authority by simply clicking a button. This privacy authority can penalise the offending website and pay you the bounty.
Other forms of privacy invasion can be achieved by colluding parties. Even tiny bits of personal information can be used to re-identify a citizen. Especially the new routing infrastructure providers for SSI and DID resolving providers may have potentially valuable information. Even though they cannot read the encrypted parts of message, they keep traffic logs of who has communicated with whom at what time. Again, countermeasure will need to combine technology and legislation.
The ugly: criminals
All benefits of SSI for citizens and legitimate businesses apply similarly to criminals and terrorists. A criminal might publish a DID/DDO on a public blockchain as advertisement how to securely communicate with its criminal business without anyone knowing who they are, except for those whom they intend to communicate with. SSI makes it fairly easy to publish a service end point for TORnet, whereas the pervasiveness of blockchain makes it hard to censor such a publication. Currently, drug dealers on the darkweb lose their reputation and sales history when a darkweb marketplace is taken down by law enforcement. SSI may enable them to keep these when migrating their business to another darkweb marketplace, or even change it entirely (“Drop gangs").
SSI technology enables the creation of webs-of-trust for citizens and legitimate businesses, but similarly for criminals. For example, a group of child-porn producers and consumers may establish a web-of-trust by using verifiable credentials to keep out law-enforcement. Public revocation registers could be used to quickly tag an account that seems to be compromised by law enforcement. Again, the pervasiveness of blockchain makes it hard to censor such a revocation. Moreover, the bilateral nature of DID pairs makes it hard to untangle a web-of-trust, legitimate or criminal.
An obvious first countermeasure will be legal intercept at the new routing infrastructure providers for SSI and DID resolving providers. Traffic patterns provide relevant information to law-enforcement for internet and telephony traffic, and it may be similarly relevant for SSI traffic. Also, criminals make mistakes. Criminals may make incorrect assumptions on who is at the other side, and messages may inadvertently be routed via the open internet instead of the dark net.
Whereas the details are hard to predict, it is likely that the cat-and-mouse game between criminals and law-enforcement is going to include SSI.
Research agenda
This blog presents a plethora of benefits of SSI technology to citizens, consumers, business, organisations and government. It also sketches potential abuse of the technology. None of these benefits and threats have already emerged, as SSI technology, its associated business models and its governance frameworks are still developing. This blog can be read as a research agenda, highlighting the functionalities that need to be achieved for the good of SSI, and against the bad and the ugly.
This blog was written in the context of the Self-Sovereign-Identity (SSI) sub-program of Techruption.
Read more about SSI technology
Read our latest in-depth articles about SSI technology
