What are those SSI standards?
"What are the relevant standards, what do they do and how do they relate?" is a question that arises when looking into ‘Self-Sovereign Identity’ (SSI) solutions. SSI adopters are confronted with a plethora of technologies and standards, ranging from decentralised public key infrastructure and transport protocols to societal concepts. It can be difficult to figure out how different technologies work and how they relate to each other. In order to help organisations with this challenge, we present an interactive graphical overview and accompanying documentation that outline the context of technologies.
We notice an increasing maturity in knowledge of Self-Sovereign Identities (SSI) within our customer base. Whereas previously we were asked what SSI is, and later on how Decentralised Identifiers (DIDs) relate to link secrets, we are now receiving questions how party X can be interoperable with party Y. To assess interoperability, one must understand the landscape of SSI-related technologies and the relation between them. However, this landscape is vast, SSI adopters are confronted with a wide variety of technologies and standards, ranging from guardianship and protection of citizens to DIDComm and KERI. To illustrate the confusion: the specification for Decentralised Identifiers (DIDs) currently lists 167 different DID method specifications that describe how DIDs are created and maintained. To outline the context for a standard, we ask ourselves:
- What does the technology described in the standard achieve?
- Is this technology compatible with or competitive to some other standard?
- Is this standard part of an interoperability profile?
Based on this information, we can divide the technologies into the four layers described in the ToIP technology stack: trust anchors, peer-to-peer connections, data exchange protocols and application ecosystems. The result is an interactive graphical overview and accompanying documentation. SSI technology stacks and interoperability profiles can be seen as vertical paths through the layers of the overview. An example of this can be seen in the overview after clicking the ‘DDIP’ or ‘AIP’ button in the graphical overview. Credential profiles could also be seen as vertical paths through the overview. A credential profile is a combination of technologies specifically used in a certain SSI solution. Based on those technologies the characteristics of the credential profile can be defined. An overview of credential profiles and their characteristics can be found in the credential comparison matrix, created at IIW and RWOT.
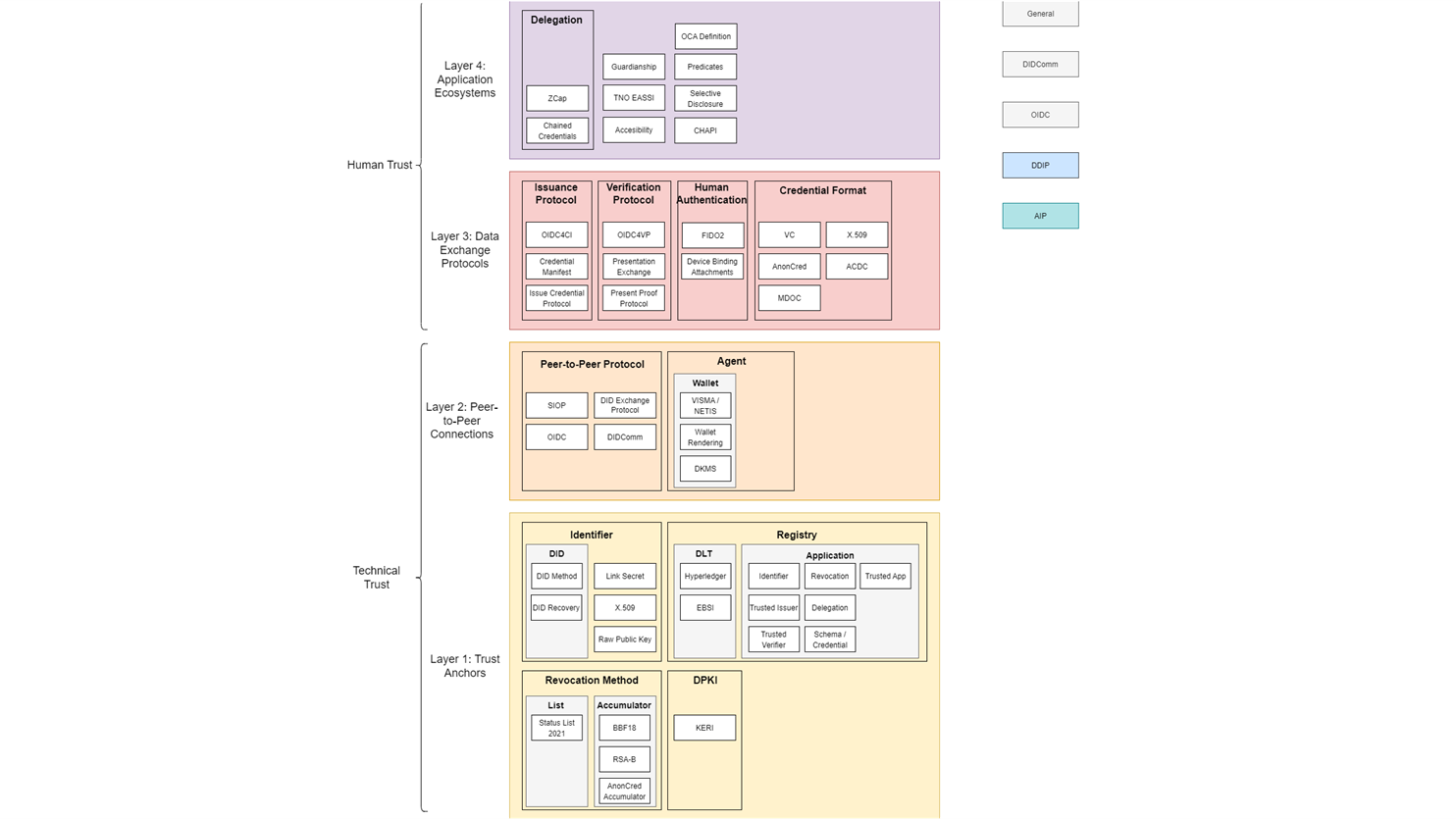
Please try the clickable interactive version here.
The infographic displays the standardisation overview. There are 4 layers visible, from bottom to top: trust anchors, peer-to-peer connections, data exchange protocols and application ecosystems. Each layer displays various standards relevant in the context of SSI. Some of the standards are grouped together in categories, for example DIDs and link secrets are both types of identifiers, hence they are listed in the category ‘Identifier’ in layer 1: trust anchors. A similar approach is taken to divide the other standards into categories and layers. The left-hand side of the infographic displays that technical trust is achieved in the first two layers, whereas in the top two layers human trust comes in. In the right top corner, buttons are displayed. In the interactive version available via the GitHub repository, these buttons can be clicked to display various connections between the standards and to which interoperability profile the standard belongs.
The standardisation landscape evolves over time. New standards are emerging and getting implemented, whereas older ones may get deprecated. Therefore we invite you to give your input. Are there any further standards in this domain that you want to understand and position? Do you have any improvements to our overview? Or are you just interested in a voice-over for this standardisation overview in the context of your application domain?
In any of such cases, please contact us!
Read more about SSI technology
Read our latest articles for professionals to see what SSI technology we have developed and how we use SSI in our projects.
